Adversarial
Simulation
By emulating real world adversarial attacks, you can assess and refine your organisation’s security defense mechanisms and processes.

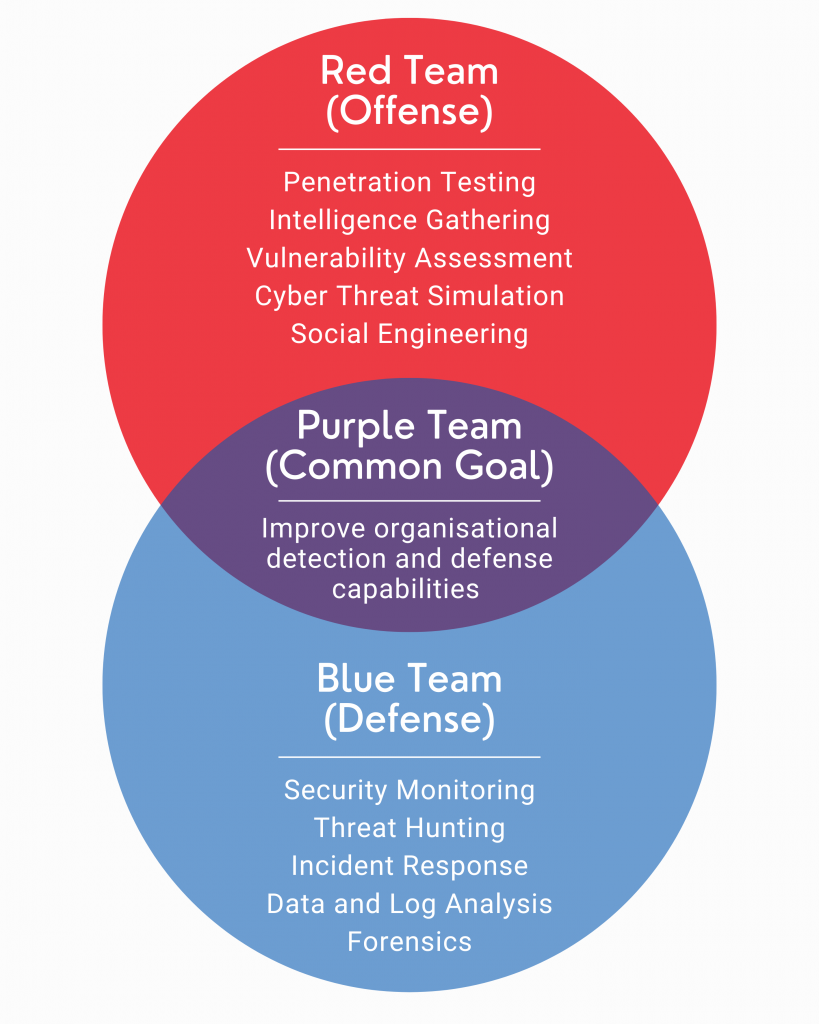
The only way to truly understand your organisation’s readiness and defense capabilities against a real world cyber attack is to emulate the Tactics, Techniques and Procedures (TTPs) used by a sophisticated threat actor.
Adversarial simulations include a variety of techniques, including ‘red teaming’ and ‘purple teaming’ which, when used in conjunction, can assess your current level of cyber resilience, the breadth of your attack surface, current response capabilities of your security operations team, and prioritise requisites for defense improvements.
JDS Adversarial Simulation Services
Related Blog Posts